Full-Blown IDE in Trickest Editor
Trickest IDE has received a new update, making it a full-blown IDE tailored for offensive security.
Introduction
The Trickest Editor has received a substantial update that improves how security professionals work. This update removes previous constraints and creates new possibilities for interacting with workflow data, monitoring execution processes, and debugging complex offensive security operations more efficiently.
The New Trickest Command Line
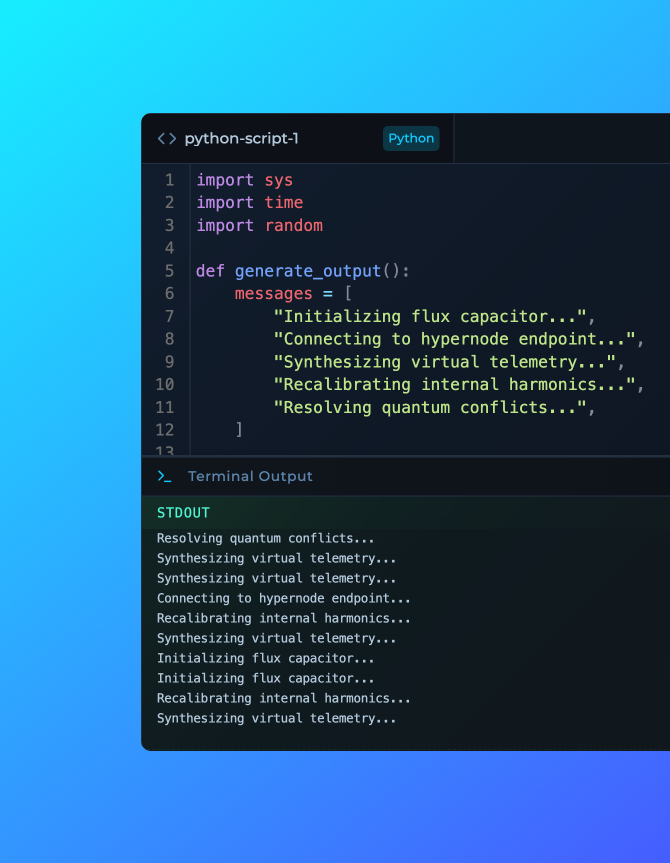
The previous CLI implementation split operational data across four separate tabs (command, outputs, stderr, stdout)—a design that created unnecessary cognitive load during active security engagements and workflow building.
The redesigned CLI now consolidates execution context into a unified interface. Command execution, stdout, and stderr appear together in a single view, while all generated outputs are accessible through a hierarchical file structure that mirrors your workflow topology.
The File Tree: Full IDE Integration for your workflows
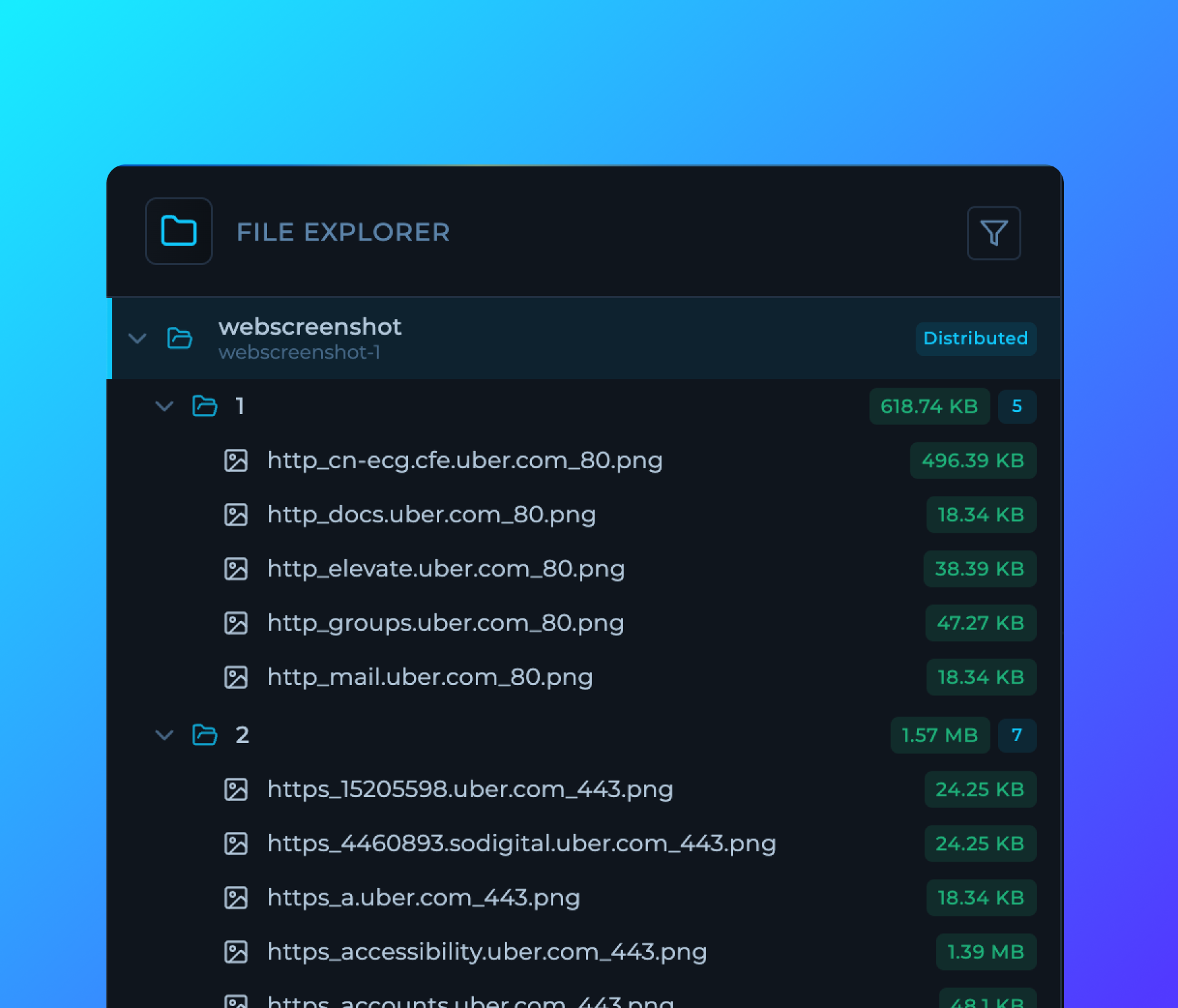
The most significant improvement is the implementation of a complete file tree structure that turns Trickest into a comprehensive IDE for offensive security workflows. Every node now has its own directory hierarchy that accurately represents the data generation patterns within the workflow, providing better visibility and control.
The file tree implements three distinct node classifications:
Distributed Nodes
Distributed nodes (distributed through file splitter) now show all parallel execution jobs and their outputs within a structured nested folder hierarchy. This update gives clear visibility into distributed nodes, offering real advantages during high-volume operations such as asset discovery or mass vulnerability scanning. Security teams can now use distributed computing with full transparency.
Regular Nodes (Tools, Scripts & Modules)
Tool, script, and module nodes present complete visibility into their execution artifacts, providing direct access to the entire file tree generated by the node.
File Tabs
The file tree implementation follows professional IDE interaction patterns:
-
Single-click access opens transient "dirty" tabs displaying file contents
-
Double-click creates persistent tabs for sustained analysis
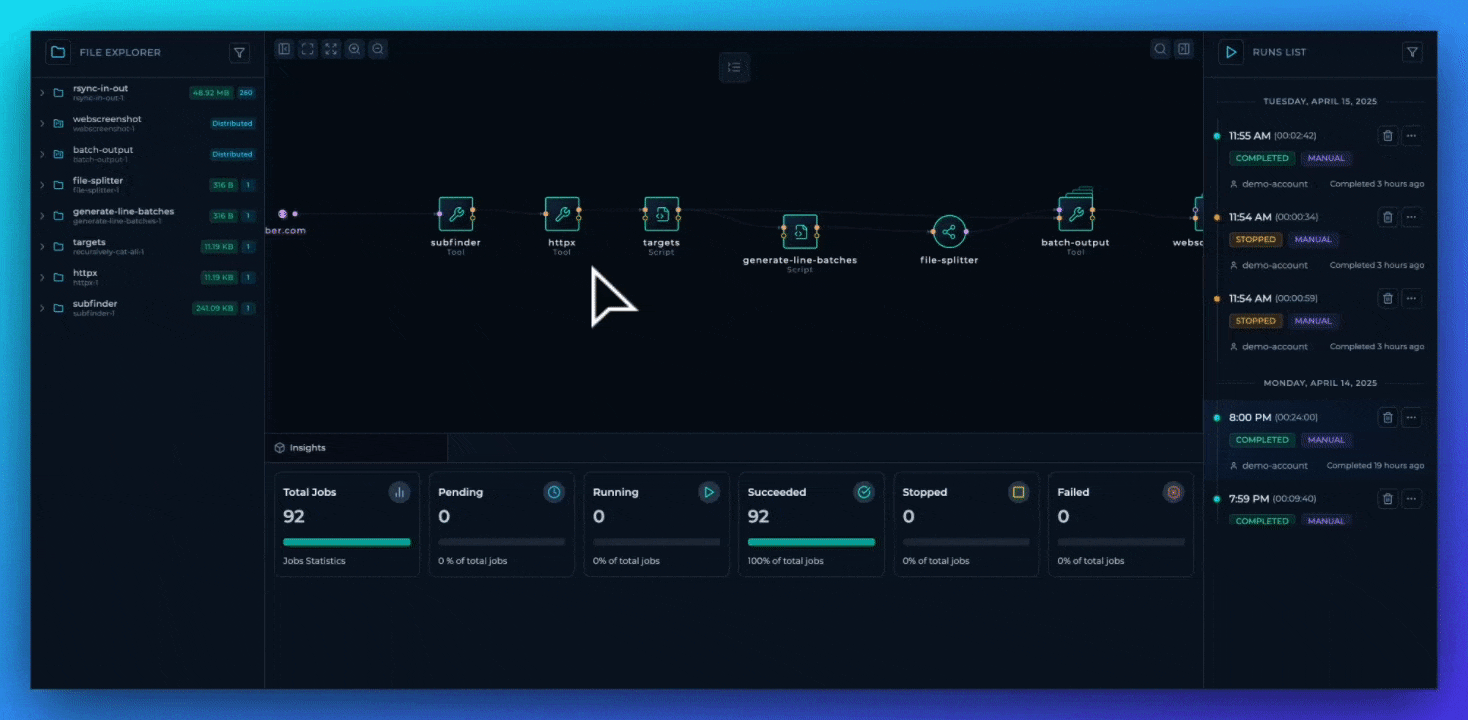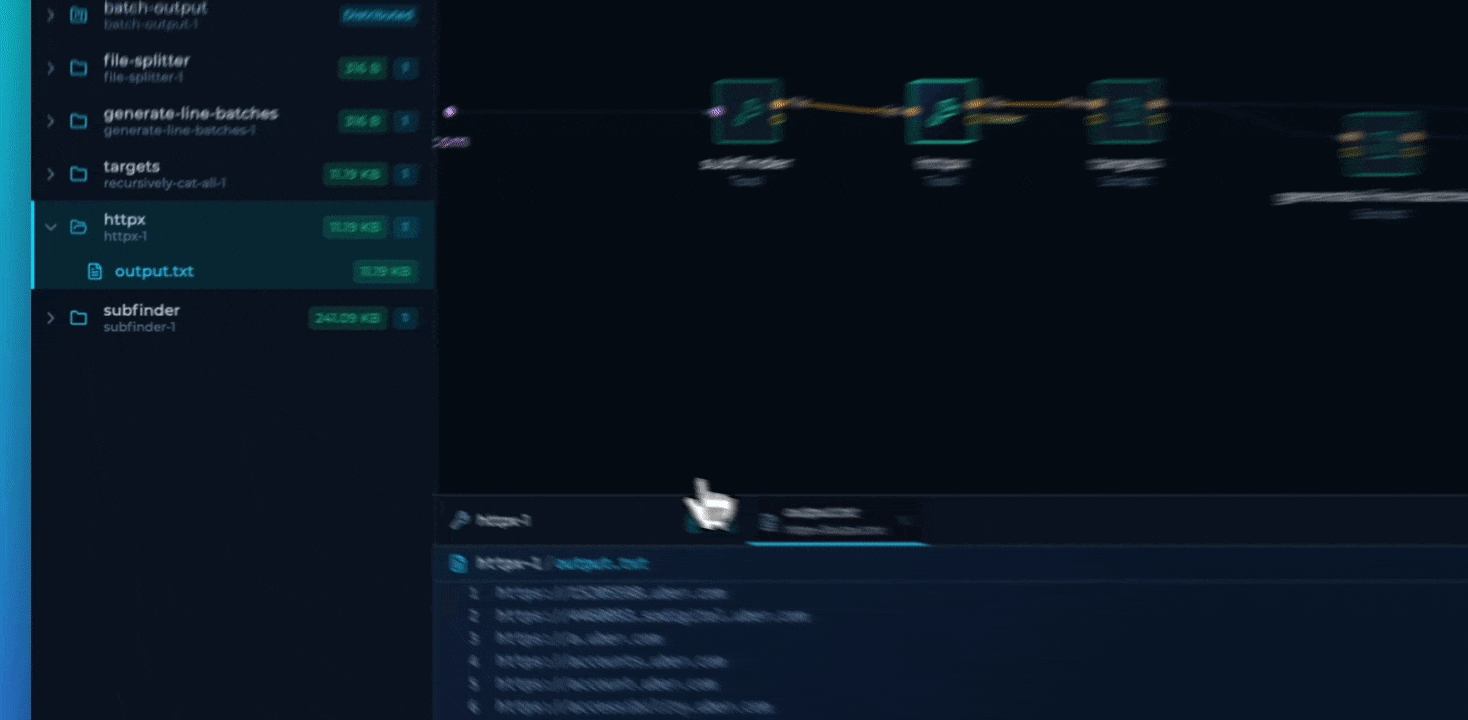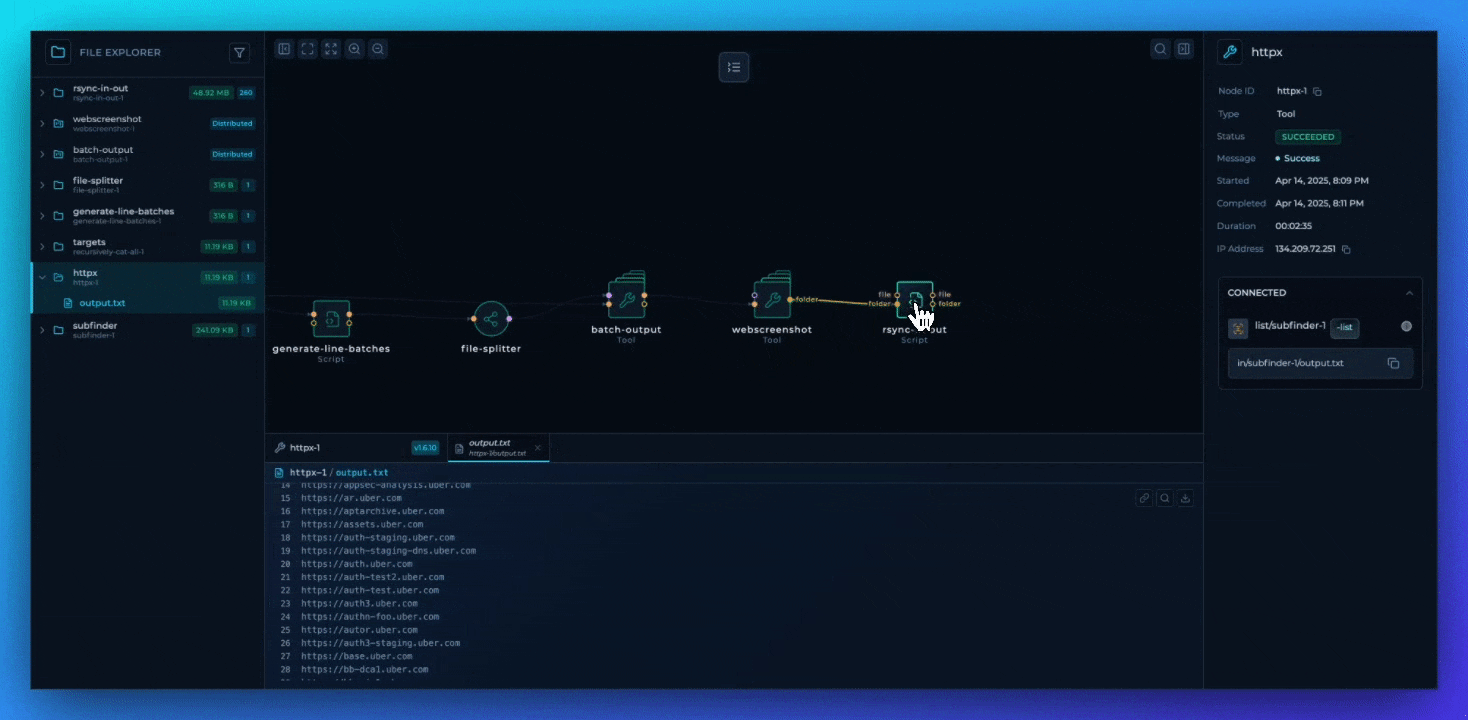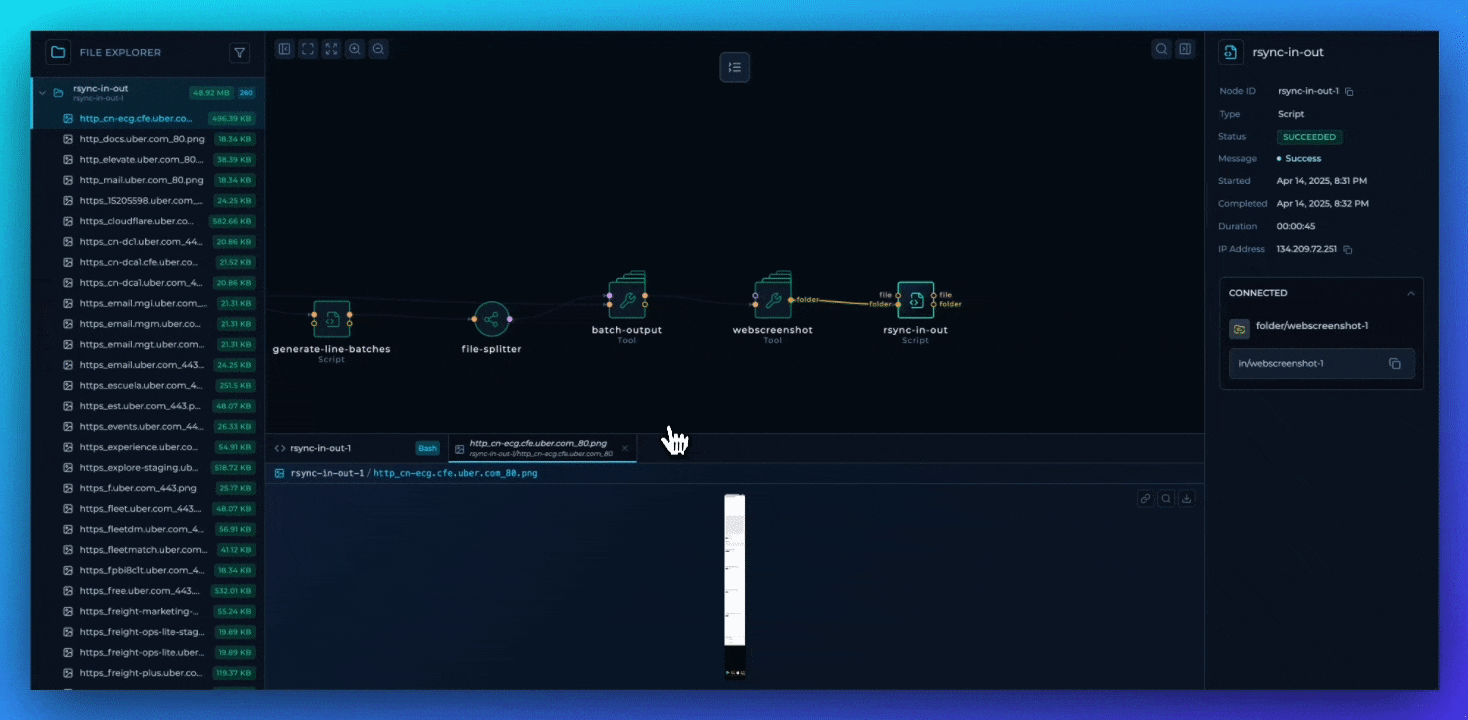
Native rendering support for binary formats, including images, enhances visualization capabilities during technical analysis.
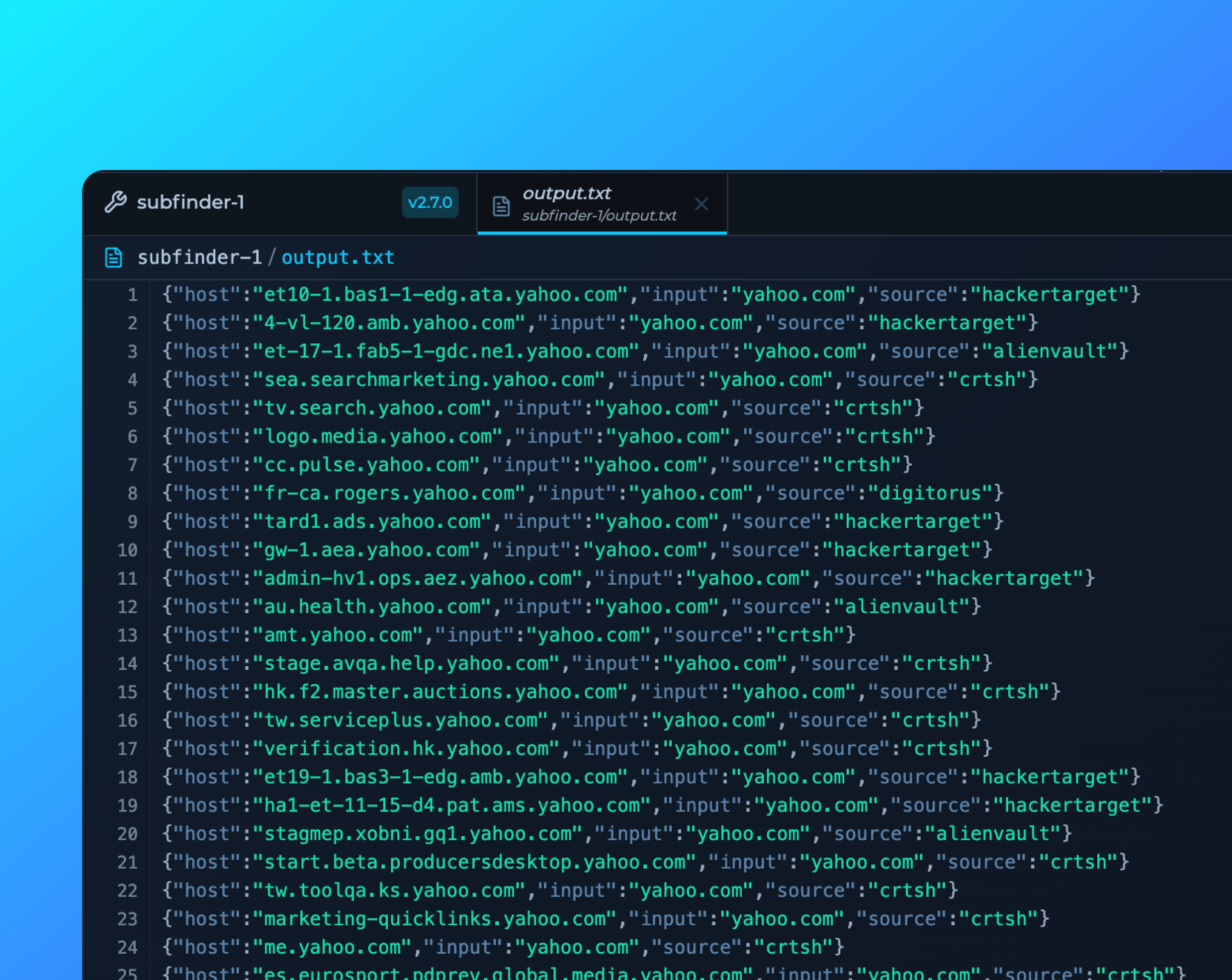
Advanced Syntax Highlighting
Syntax highlighting has been implemented for all major programming languages and structured data formats (JSON, XML, YAML), improving code readability during analysis and development. This enhancement makes examining complex output structures or developing custom offensive modules easier, helping you recognize code patterns quickly and reducing analysis time.
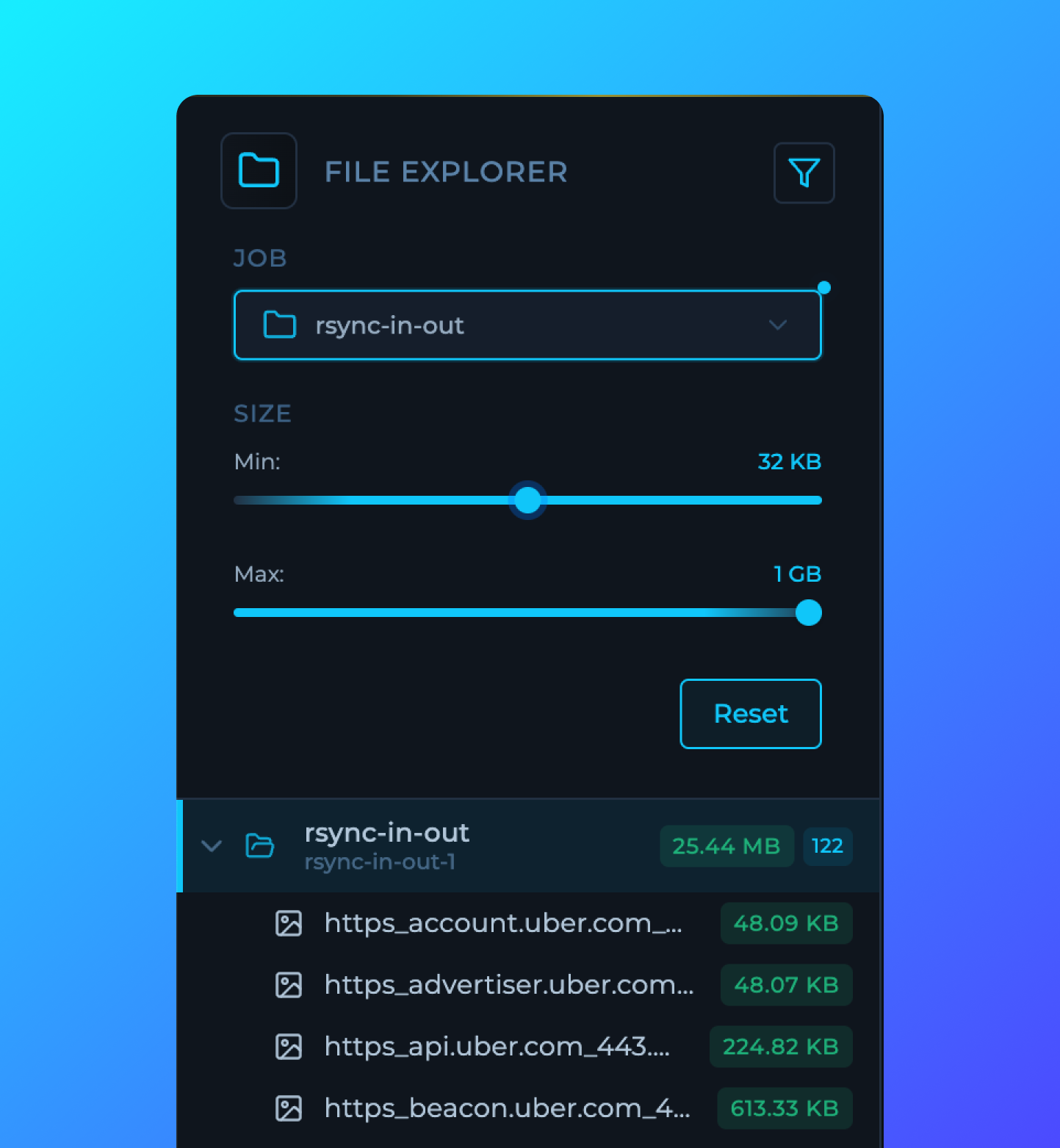
Output Filtering
Each folder node now offers output filtering through file size threshold controls. This capability improves how teams work with large-scale scan outputs, enabling security professionals to target and isolate outputs based on size characteristics—a useful advantage when hunting specific patterns in large datasets. This feature can cut analysis time considerably in complex security operations.
Technical Impact & Future Potential
These architectural updates improve Trickest beyond a workflow orchestration tool, turning it into a complete offensive security development environment.
The implementation delivers clear benefits:
- Eliminating context-switching during node changes
- Better visibility into distributed execution processes
- Precise output filtering for faster data analysis
For offensive security professionals, these improvements mean faster automation building, more effective operations, and improved debugging capabilities during complex workflow creation and execution.
For more updates check out our changelog, or talk with us to see the Trickest Editor in action!
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
